In today's interconnected digital landscape, cybersecurity stands as a critical pillar for businesses of all sizes. As technology advances, so do the methods of cyber threats, making it imperative for organizations to understand the nuanced balance between risk and investment in cybersecurity measures. This blog aims to shed light on the financial implications of cybersecurity decisions, providing valuable insights for businesses navigating this complex terrain.
Importance of Cybersecurity in Today's Business Landscape
The pervasiveness of digital technologies in business operations has led to an exponential rise in cyber threats. From sophisticated hacking attempts to ransomware attacks, organizations face an array of risks that can compromise sensitive data, disrupt operations, and tarnish reputation. As such, prioritizing cybersecurity is no longer an option but a necessity for survival and sustainability in the modern marketplace.
Overview of the Concept of Risk vs. Investment in Cybersecurity
The concept of risk vs. investment in cybersecurity revolves around the delicate balance between safeguarding assets and allocating resources effectively. It involves evaluating potential threats, assessing vulnerabilities, and determining the most strategic allocation of financial resources to mitigate risks. By understanding this balance, businesses can make informed decisions that maximize security while optimizing return on investment.
This blog seeks to demystify the financial aspects of cybersecurity, empowering businesses to make informed decisions that align with their strategic objectives. By delving into the nuances of risk assessment, investment calculation, and stakeholder communication, it aims to equip organizations with the knowledge needed to navigate the complex landscape of cybersecurity investments effectively.
Understanding Cybersecurity Risk
Cybersecurity risk refers to the potential for loss or harm resulting from cyber threats such as data breaches, malware attacks, and phishing scams. It encompasses both the likelihood of an attack occurring and the magnitude of its potential impact on business operations, financial assets, and reputation.
Common Threats Faced by Businesses
Businesses face a myriad of cyber threats, ranging from external attacks by malicious actors to internal vulnerabilities stemming from inadequate security protocols. These threats include malware infections, data breaches, ransomware attacks, phishing attempts, and insider threats, each posing unique challenges to organizational security and resilience.
Financial and Reputational Consequences of Cyber Attacks
The financial and reputational consequences of cyber attacks can be devastating for businesses. Beyond the immediate costs of remediation and recovery, organizations may incur significant financial losses due to theft of sensitive data, disruption of operations, regulatory fines, and legal liabilities. Moreover, the damage to reputation and loss of customer trust can have far-reaching implications that impact long-term profitability and sustainability.
Calculating the Cost of Cybersecurity Investment
Factors to Consider When Assessing Cybersecurity Investment
When assessing cybersecurity investment, businesses must consider various factors to determine the most effective allocation of resources. These factors include the cost of cybersecurity tools and technologies, potential savings from avoiding data breaches, and the impact on productivity and efficiency.
- Cost of Cybersecurity Tools and Technologies: Investing in robust cybersecurity solutions entails upfront costs for acquiring software, hardware, and infrastructure upgrades. Organizations must weigh the initial investment against the long-term benefits of enhanced security and risk mitigation.
- Potential Savings from Avoiding Data Breaches: By investing in cybersecurity measures, businesses can mitigate the risk of data breaches and associated financial losses. Calculating the potential savings from avoiding data breaches involves assessing the probability of an attack occurring and the magnitude of its potential impact on business operations and assets.
- Impact on Productivity and Efficiency: Effective cybersecurity measures can enhance productivity and efficiency by minimizing downtime, streamlining processes, and safeguarding critical assets. Organizations must consider the indirect costs and benefits of cybersecurity investment in terms of operational performance and business continuity.
Methods for Quantifying Cybersecurity ROI
Quantifying the return on investment (ROI) of cybersecurity initiatives requires a systematic approach that takes into account both tangible and intangible factors. Two common methods for quantifying cybersecurity ROI are cost-benefit analysis and ROI calculations.
- Cost-Benefit Analysis: Cost-benefit analysis involves comparing the costs of implementing cybersecurity measures with the anticipated benefits in terms of risk reduction, cost savings, and operational improvements. By quantifying the costs and benefits associated with cybersecurity investment, organizations can make informed decisions that maximize ROI.
- Return on Investment (ROI) Calculations: ROI calculations measure the financial return generated by cybersecurity investments relative to the initial cost of implementation. By analyzing the net benefits over a specified time period, organizations can assess the effectiveness of their cybersecurity initiatives and prioritize future investments accordingly.
Making the Business Case for Cybersecurity Investment
- Communicating the Importance of Cybersecurity to Stakeholders: Effectively communicating the importance of cybersecurity to stakeholders is essential for garnering support and securing resources for investment. This involves raising awareness of the potential risks and consequences of cyber threats, highlighting the strategic value of cybersecurity initiatives, and fostering a culture of security throughout the organization.
- Aligning Cybersecurity Goals with Business Objectives: Aligning cybersecurity goals with business objectives is crucial for ensuring that investments are strategically aligned with organizational priorities. By identifying key business drivers and aligning cybersecurity initiatives with overarching goals such as revenue growth, cost reduction, and regulatory compliance, organizations can demonstrate the tangible value of security investments to stakeholders.
Presenting a Compelling Financial Argument for Investment in Cybersecurity Measures
Presenting a compelling financial argument for investment in cybersecurity measures requires a thorough understanding of the cost-benefit analysis and ROI calculations. By articulating the potential return on investment, quantifying the financial impact of cyber threats, and highlighting the long-term benefits of security investments, organizations can make a compelling case for allocating resources to cybersecurity initiatives.
Strategies for Effective Cybersecurity Investment
Prioritizing Cybersecurity Initiatives Based on Risk Assessment
Prioritizing cybersecurity initiatives based on risk assessment involves identifying and prioritizing vulnerabilities, threats, and potential impacts on business operations. By focusing resources on high-risk areas and implementing targeted security measures, organizations can maximize the effectiveness of their cybersecurity investments and mitigate the most significant threats.
Implementing a Layered Approach to Cybersecurity
Implementing a layered approach to cybersecurity involves deploying multiple layers of defense to protect against a wide range of threats. This includes perimeter security measures such as firewalls and intrusion detection systems, endpoint security solutions such as antivirus software and device encryption, and data protection measures such as encryption and access controls. By adopting a multi-faceted approach to security, organizations can create overlapping layers of protection that enhance resilience and minimize the risk of successful cyber attacks.
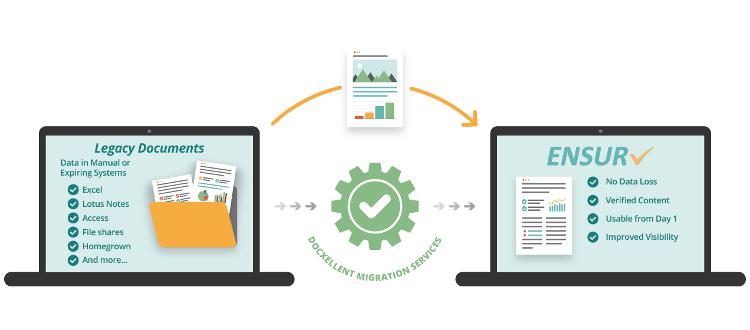
Leveraging Cost-Effective Solutions Such as a Document Management System (DMS)
In addition to prioritizing cybersecurity initiatives and implementing a layered approach to security, businesses can further optimize their cybersecurity investment by leveraging cost-effective solutions such as a Document Management System (DMS). A DMS offers a centralized platform for storing, managing, and securing documents and files, providing organizations with greater control over their information assets.
ENSUR Lite emerges as a standout solution for businesses seeking a DMS that balances functionality, affordability, and ease of use. Tailored specifically for small and medium-sized businesses (SMBs), ENSUR Lite offers a simplified yet robust document management platform designed to streamline workflows, enhance collaboration, and improve document security.
Benefits of Using ENSUR Lite for SMBs
For SMBs, the benefits of adopting ENSUR Lite as a DMS solution are manifold:
- Affordability: ENSUR Lite offers a cost-effective alternative to expensive enterprise-grade DMS solutions, making it accessible to SMBs with limited budgets. With transparent pricing and flexible licensing options, ENSUR Lite ensures that organizations can implement a comprehensive document management solution without overspending.
- Ease of Use: ENSUR Lite boasts an intuitive user interface and user-friendly features that simplify document management tasks for non-technical users. From document creation and editing to version control and file sharing, ENSUR Lite streamlines workflows and minimizes the learning curve, allowing users to maximize productivity without extensive training.
- Scalability: As SMBs grow and evolve, their document management needs may change. ENSUR Lite offers scalability and flexibility to accommodate expanding document volumes, user populations, and organizational requirements. With scalable storage options and customizable features, ENSUR Lite adapts to the changing needs of SMBs without disrupting operations or incurring additional costs.
- Security: In today's threat landscape, ensuring the security of sensitive documents and data is paramount. ENSUR Lite incorporates robust security features such as access controls, encryption, audit trails, and user authentication to safeguard confidential information from unauthorized access, data breaches, and cyber threats. By implementing ENSUR Lite as their DMS solution, SMBs can enhance document security and compliance with regulatory requirements, minimizing the risk of data loss or exposure.
- Compliance: Many SMBs operate in highly regulated industries where compliance with industry-specific regulations and standards is mandatory. ENSUR Lite helps SMBs achieve and maintain compliance with regulatory requirements such as GDPR, HIPAA, SOX, and ISO standards by providing tools and features that facilitate document management, retention, and audit trails. By ensuring compliance with regulatory mandates, ENSUR Lite enables SMBs to mitigate legal and financial risks associated with non-compliance and uphold the trust and confidence of their customers and stakeholders.
ENSUR Lite offers SMBs a cost-effective, user-friendly, and feature-rich DMS solution that addresses their document management needs while enhancing security, compliance, and productivity. By leveraging ENSUR Lite as part of their cybersecurity strategy, SMBs can optimize their investment in cybersecurity and safeguard their critical information assets against evolving cyber threats.
As businesses navigate the ever-changing threat landscape, it is imperative to prioritize cybersecurity as a strategic investment that aligns with organizational goals and objectives. By investing in robust cybersecurity measures, businesses can mitigate risks, protect assets, and maintain trust and confidence in an increasingly digital world.
Get Started Today
For businesses seeking to enhance their cybersecurity posture and streamline document management processes, resources such as the ENSUR Lite guide offer valuable insights and guidance. By leveraging cost-effective solutions like ENSUR Lite, businesses can optimize their cybersecurity investment and achieve greater efficiency, security, and compliance in managing their critical information assets.